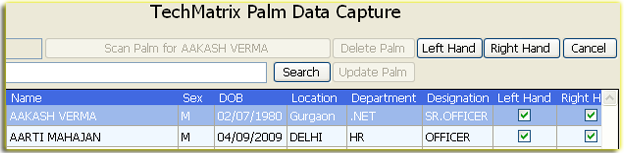
- A palm print identification system in which an image of the palm pattern is optically
formed and scanned to generate a video signal which is an analog of the pattern,
the signal being converted into a numerical code. Because each palm print is unique,
an individual is thereby given a singular identifying code number which is an index
to the pattern.
- The pattern of blood veins is unique to every individual, even among identical twins.
Palms have a broad and complicated vascular pattern and thus contain a wealth of
differentiating features for personal identification. Furthermore, it will not vary
during the person's lifetime.
- It is a very secure method of authentication because this blood vein pattern lies
under the skin. This makes it almost impossible for others to read or copy.
- An individual's vein pattern image is captured by radiating his/her hand with near-infrared
rays.
- The reflection method illuminates the palm using an infrared ray and captures the
light given off by the region after diffusion through the palm.
- The deoxidized hemoglobin in the in the vein vessels absorbs the infrared ray, thereby
reducing the reflection rate and causing the veins to appear as a black pattern.
This vein pattern is then verified against a reregistered pattern to authenticate
the individual.
- As veins are internal in the body and have a wealth of differentiating features,
attempts to forge an identity are extremely difficult, thereby enabling a high level
of security.
|